Cisco IOS devices typically use their flash memory to store the IOS image. On most routers, this flash memory can be easily replaced. On some switches, it is integrated in the device and can’t be replaced.
In this lesson, I’ll show you some different options how to copy a new IOS image to your Cisco IOS router or switch. I will use a Cisco 2800 IOS router in these examples.
First, head over to Cisco.com > Support > Download and grab the IOS image that you want. For example:
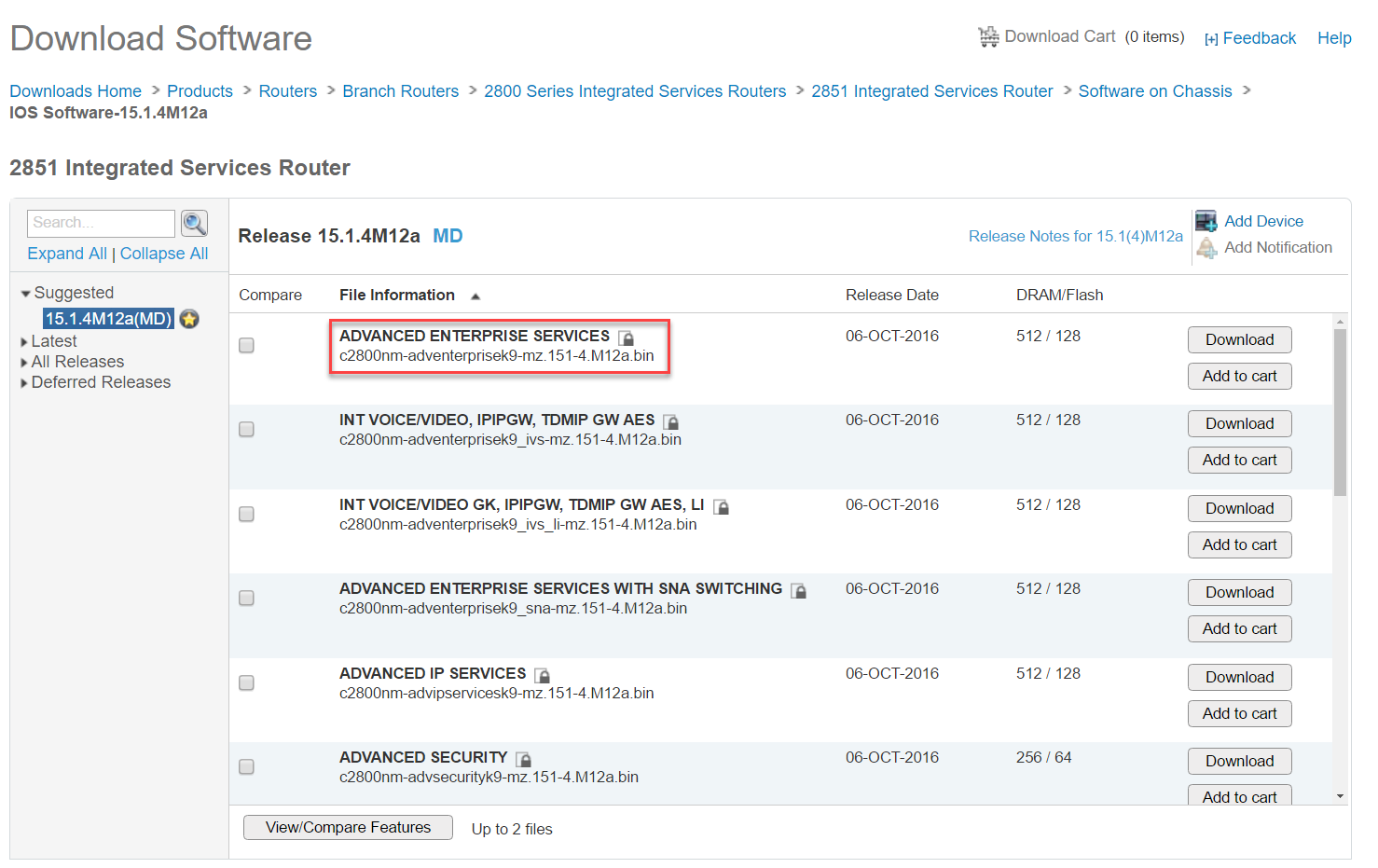
If you hover your mouse over the filename, you will see some extra information:
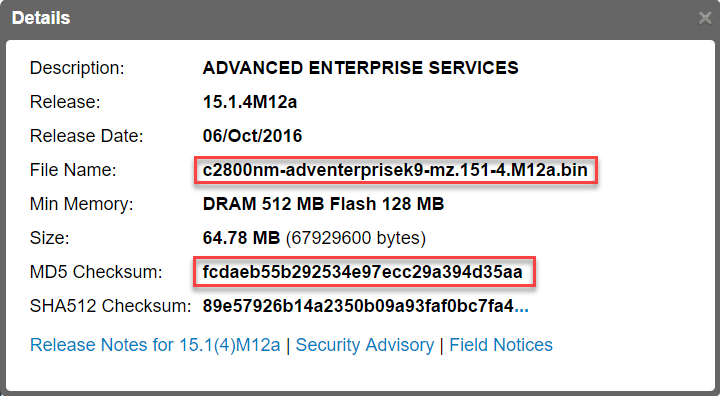
Above you can see the file name and MD5 checksum. The checksum can be used to check if the file that you downloaded is the same or has changed. I’ll show you this later.
Once you downloaded the IOS image, check if you have enough space left on your flash memory:
R1#show flash: -#- --length-- -----date/time------ path
1 1119 Sep 29 2015 11:11:52 +00:00 r1-r2-r3.cfg
2 1184 Dec 3 2014 15:14:06 +00:00 R1-R2-ASA1-ASA2.cfg
3 1125 Dec 23 2014 13:41:32 +00:00 ASA1-R1-R2-R3.cfg
5 76 Jul 17 2014 12:09:10 +00:00 System Volume Information/IndexerVolumeGuid
6 1060 Aug 11 2015 12:53:50 +00:00 mpls-pe-ce-basic-addressing.cfg
7 1213 Sep 30 2015 15:05:02 +00:00 router-on-a-stick.cfg
8 67926080 Apr 2 2015 14:21:46 +00:00 c2800nm-adventerprisek9-mz.151-4.M10.bin
3862364160 bytes available (137428992 bytes used)On my flash memory, there are a bunch of configuration files and the current IOS image. There are 3862364160 bytes available (3862 MB) so we have plenty of space.
When we want to copy something to or from this router, we have to use the copy command:
R1#copy ? /erase Erase destination file system.
/error Allow to copy error file.
/noverify Don't verify image signature before reload.
/verify Verify image signature before reload.
archive: Copy from archive: file system
cns: Copy from cns: file system flash: Copy from flash: file system ftp: Copy from ftp: file system http: Copy from http: file system
https: Copy from https: file system
null: Copy from null: file system
nvram: Copy from nvram: file system
pram: Copy from pram: file system
rcp: Copy from rcp: file system
running-config Copy from current system configuration scp: Copy from scp: file system startup-config Copy from startup configuration
system: Copy from system: file system
tar: Copy from tar: file system tftp: Copy from tftp: file system tmpsys: Copy from tmpsys: file system
xmodem: Copy from xmodem: file system
ymodem: Copy from ymodem: file systemWe have a lot of options. The most common options for copying an IOS image are:
- TFTP
- FTP
- SCP
I will explain all three options to you.
TFTP
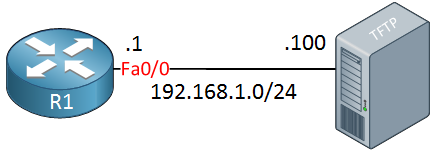
TFTP (Trivial File Transfer Protocol) is similar to FTP but much simpler, like a light weight version. It doesn’t support authentication or encryption and uses UDP for transmission. I will use the following topology:
We need a TFTP server application, a great choice here is TFTPD32. You can download it for free and it’s an executable, no need to install anything.
Once you downloaded TFTPD32, start it:
And you will see the main screen:
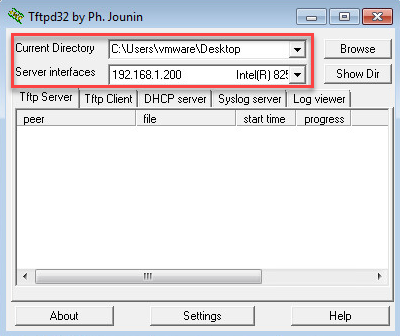
Make sure you select the correct directory where you downloaded your IOS image and if you have multiple network interfaces, select the correct interface.
The copy command works in both directions. I can copy to and from the TFTP server. Here’s how to copy the current IOS image to the TFTP server:
R1#copy flash: tftp: Source filename []? c2800nm-adventerprisek9-mz.151-4.M10.bin Address or name of remote host []? 192.168.1.200 Destination filename [c2800nm-adventerprisek9-mz.151-4.M10.bin]?
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
67926080 bytes copied in 312.508 secs (217358 bytes/sec)When you use the copy flash: tftp: command, it will ask you for the IP address and filename. When you see something between [] (brackets), you can just hit the enter button. For example, since I specified the source name, the router assumes I want to use the same file name for the destination. Don’t type “y†or “yes†here or that will become the destination filename.
We can see the transfer on our router or you can see it in TFTPD32:
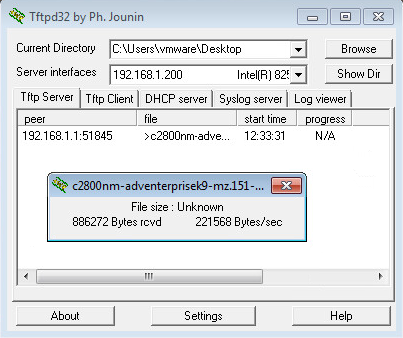
We now have a backup of our current IOS image. Let’s copy the new image to the router:
R1#copy tftp: flash: Address or name of remote host []? 192.168.1.200 Source filename []? c2800nm-adventerprisek9-mz.151-4.M12a.bin Destination filename [c2800nm-adventerprisek9-mz.151-4.M12a.bin]?
Accessing tftp://192.168.1.200/c2800nm-adventerprisek9-mz.151-4.M12a.bin...
Loading c2800nm-adventerprisek9-mz.151-4.M12a.bin from 192.168.1.200 (via FastEthernet0/0): !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
[OK - 67929600 bytes]
67929600 bytes copied in 316.628 secs (214541 bytes/sec)The transfer has completed, let’s take a look at our flash memory:
R1#show flash: | include .bin 8 67926080 Apr 2 2015 14:21:46 +00:00 c2800nm-adventerprisek9-mz.151-4.M10.bin
25 67929600 Nov 4 2016 12:11:22 +00:00 c2800nm-adventerprisek9-mz.151-4.M12a.binAbove we can see the new IOS image.
The copy command also allows you to enter parameters like the IP address of the TFTP server and filenames. Here is an example:
R1#copy tftp://192.168.1.200/c2800nm-adventerprisek9-mz.151-4.M12a.bin flash: Destination filename [c2800nm-adventerprisek9-mz.151-4.M12a.bin]?Above you can see that I already entered the IP address and filename. Once I hit enter, it will only ask me for the destination filename (which I also could have entered). If you have to upgrade the IOS image on multiple devices, this is more convenient as you can just copy/paste the above line on all devices.
You can also turn a Cisco IOS router or switch into a TFTP server. You only need one command to accomplish this:
R1(config)#tftp-server flash:c2800nm-advipservicesk9-mz.124-24.T8.bin alias 2800-image.binThe alias parameters lets you use a different name for the filename. In the example above, “2800-image.bin†refers to the actual file on the flash of my router.
FTP
Copying to or from an FTP server is also no problem, we can do this with the same copy command. One thing you might have to deal with is authentication. Most FTP servers will require a username and password. Here is the topology I will use:
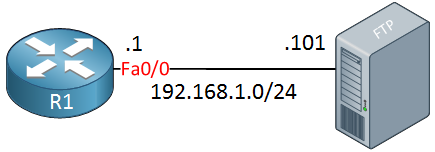
There are two things we can do to supply a username and password. Here is option one::
R1(config)#ip ftp username admin R1(config)#ip ftp password ciscoWe can globally configure the username and password that we want to use for the FTP server. When you use the copy command, Cisco IOS will use these values for authentication.
Personally, I don’t like leaving this information in the running configuration. It’s also possible to supply a username and password with the copy command. Here is an example:
R1#copy ftp://admin:cisco@192.168.1.201/c2800nm-adventerprisek9-mz.151-4.M12a.bin flash: Destination filename [c2800nm-adventerprisek9-mz.151-4.M12a.bin]?
Accessing ftp://*****:*****@192.168.1.201/c2800nm-adventerprisek9-mz.151-4.M12a.bin...
Loading c2800nm-adventerprisek9-mz.151-4.M12a.bin from 192.168.1.201 (via FastEthernet0/0): !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
[OK - 67929600 bytes]
67929600 bytes copied in 884.704 secs (76782 bytes/sec)Above you can see I embedded the username “adminâ€, the password “cisco†and the IP address of my FTP server. This way is also easier, you can copy/paste this line on all devices that require an IOS image upgrade.
SCP
Last but not least, we have SCP (Secure Copy) which uses SSH. This is a great method because of two reasons:
- It allows you to use your router/switch as an SCP server.
- It uses encryption.
- You probably already have SSH configured on your router or switch.
I will show you how to configure your router as an SCP server and how to copy files to/from it. I’m going to use two routers for this:
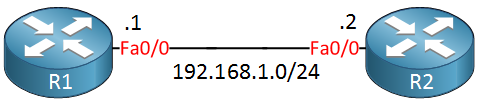
R1 Configuration
First, we have to configure SSH:
R1(config)#ip domain-name NETWORKLESSONS.LOCAL R1(config)#line vty 0 4 R1(config-line)#transport input ssh R1(config-line)#login local R1(config)#crypto key generate rsa The name for the keys will be: R1.NETWORKLESSONS.LOCAL
Choose the size of the key modulus in the range of 360 to 4096 for your
General Purpose Keys. Choosing a key modulus greater than 512 may take
a few minutes.
How many bits in the modulus [512]: 1024 % Generating 1024 bit RSA keys, keys will be non-exportable...
[OK] (elapsed time was 3 seconds)
R1(config)#ip ssh version 2Now we only need two additional commands for SCP. The first one is to enable the SCP server:
R1(config)#ip scp server enableAnd we need a user that has full access to the router:
R1(config)#username admin privilege 15 password ciscoLet’s continue with R2, our SCP client.
R2 Configuration
R2 will be our SCP client. Let’s try the copy command:
R2#copy scp: flash: Address or name of remote host []? 192.168.1.1
Source username []? admin
Source filename []? c2800nm-adventerprisek9-mz.151-4.M12a.bin
Destination filename [c2800nm-adventerprisek9-mz.151-4.M12a.bin]?
Password:
!!!!!!!!!!!
67929600 bytes copied in 884.704 secs (76782 bytes/sec)The copy command will ask for the remote IP address, username, password, and filename.
MD5 Verification
So far we copied a couple of files but how do we know that these files are valid? When we downloaded the Cisco IOS image, I showed you the MD5 checksum that Cisco publishes on their website. We can verify this checksum on our router:
R1#verify /md5 flash:c2800nm-adventerprisek9-mz.151-4.M12a.bin .................Done!
verify /md5 (flash:c2800nm-adventerprisek9-mz.151-4.M12a.bin) = fcdaeb55b292534e97ecc29a394d35aaThis MD5 checksum is the same as the one we found on the Cisco website. This tells us that we have the same file as Cisco published and that the file has not been tampered with. If the checksum fails, maybe someone has added something nasty to the image.
Boot System
Our router currently has two IOS images:
R1#show flash: | include .bin 8 67926080 Apr 2 2015 14:21:46 +00:00 c2800nm-adventerprisek9-mz.151-4.M10.bin
25 67929600 Nov 4 2016 12:11:22 +00:00 c2800nm-adventerprisek9-mz.151-4.M12a.binWhich IOS image will it select when the router boots? Deleting the old IOS image is one option but there is another way.
Most routers will select the first filename that they find on the flash memory so in our case, it means it would boot the older IOS image. We can change this with the boot sytem command:
R1(config)#boot system flash:c2800nm-adventerprisek9-mz.151-4.M12a.binLet’s reload the router:
R1#reload System configuration has been modified. Save? [yes/no]: yes Building configuration...
[OK]Once the router has reloaded, verify that we are running the new IOS image:
R1#show version
Cisco IOS Software, 2800 Software (C2800NM-ADVENTERPRISEK9-M), Version 15.1(4)M12a, RELEASE SOFTWARE (fc1)
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2016 by Cisco Systems, Inc.
Compiled Tue 04-Oct-16 03:37 by prod_rel_team
ROM: System Bootstrap, Version 12.4(13r)T, RELEASE SOFTWARE (fc1)
R1 uptime is 14 minutes
System returned to ROM by reload at 14:01:00 UTC Fri Nov 4 2016
System image file is "flash:c2800nm-adventerprisek9-mz.151-4.M12a.bin"Above we can see we booted the new Cisco IOS image.

 Английский
Английский Русский
Русский